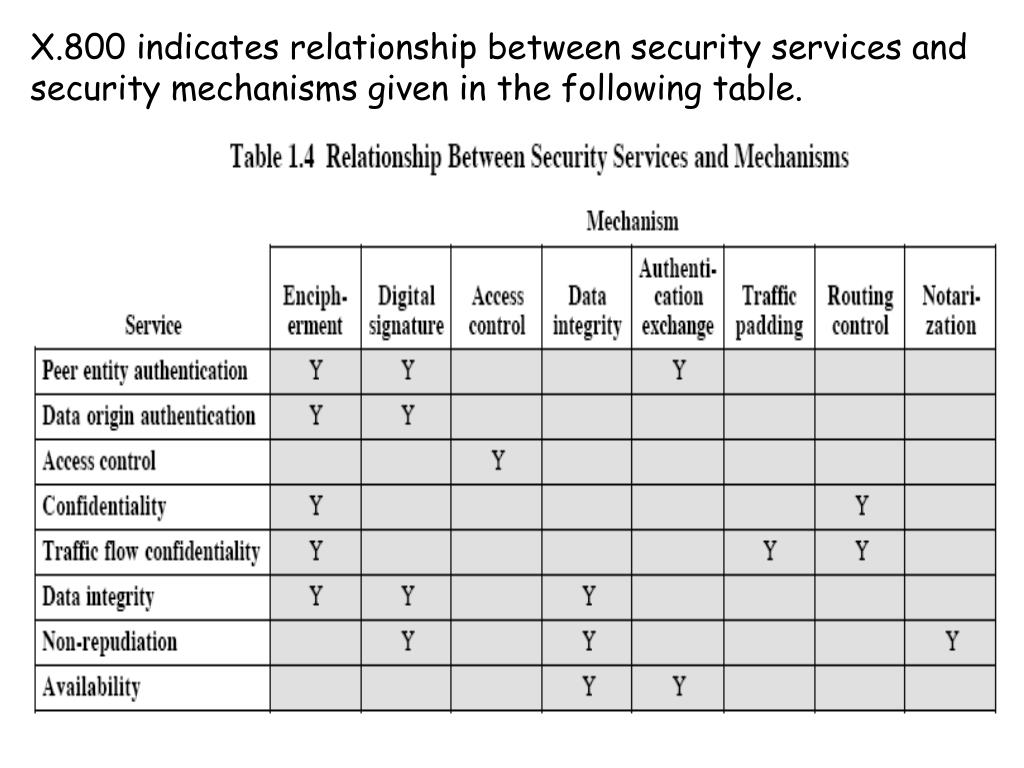
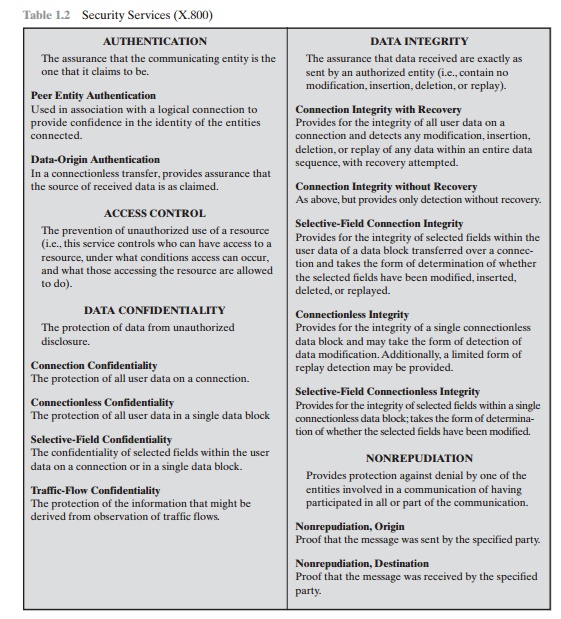
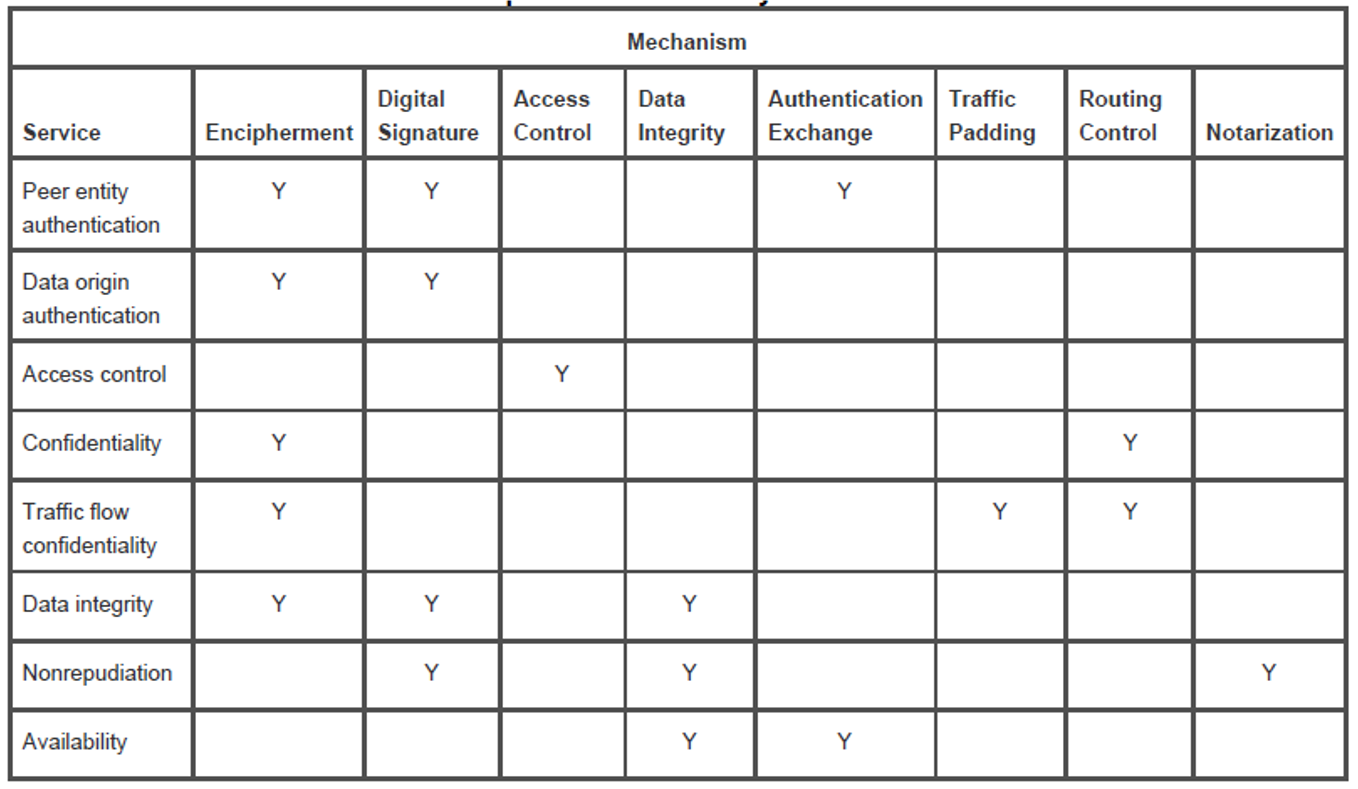
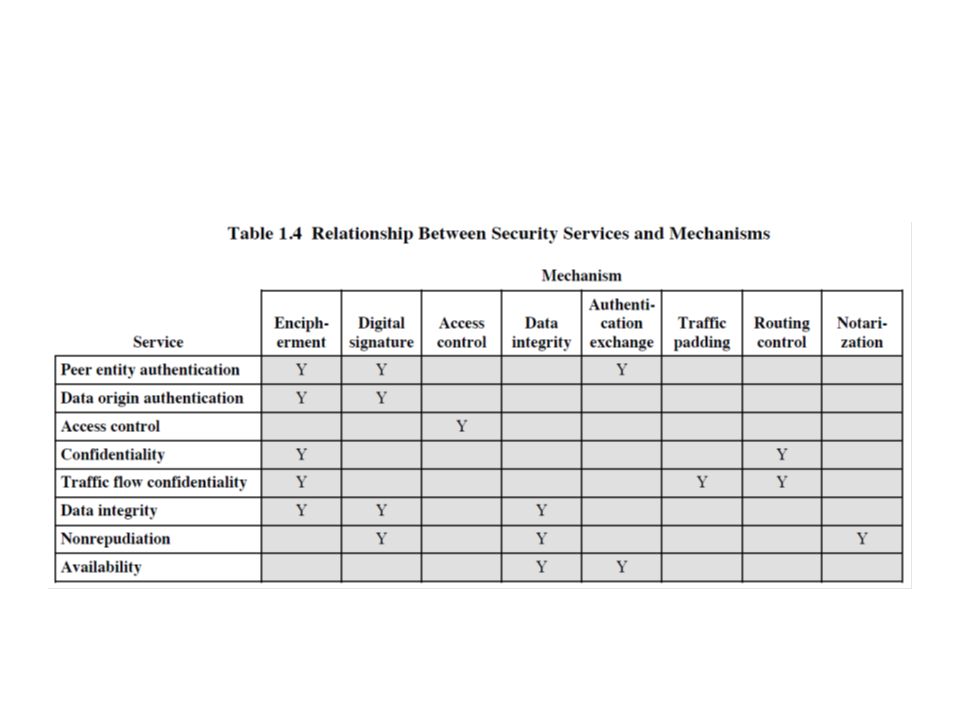
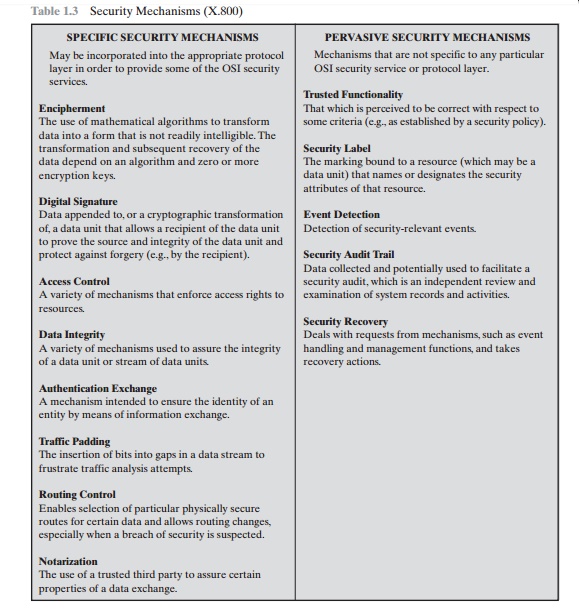
CryptographyBhutan - Lesson 12 #securitymechanism #securityservices Security services are implemented by a security mechanism or combination of mechanisms: 1. Peer entity authentication service can be implemented by or combination of Encipherment, Digital
CS480 Cryptography and Information Security Huiping Guo Department of Computer Science California State University, Los Angeles Course administration. - ppt download
Assignment1.docx - 1 Consider a desktop publishing system used to produce documents for various organizations a Given an example of a type of | Course Hero
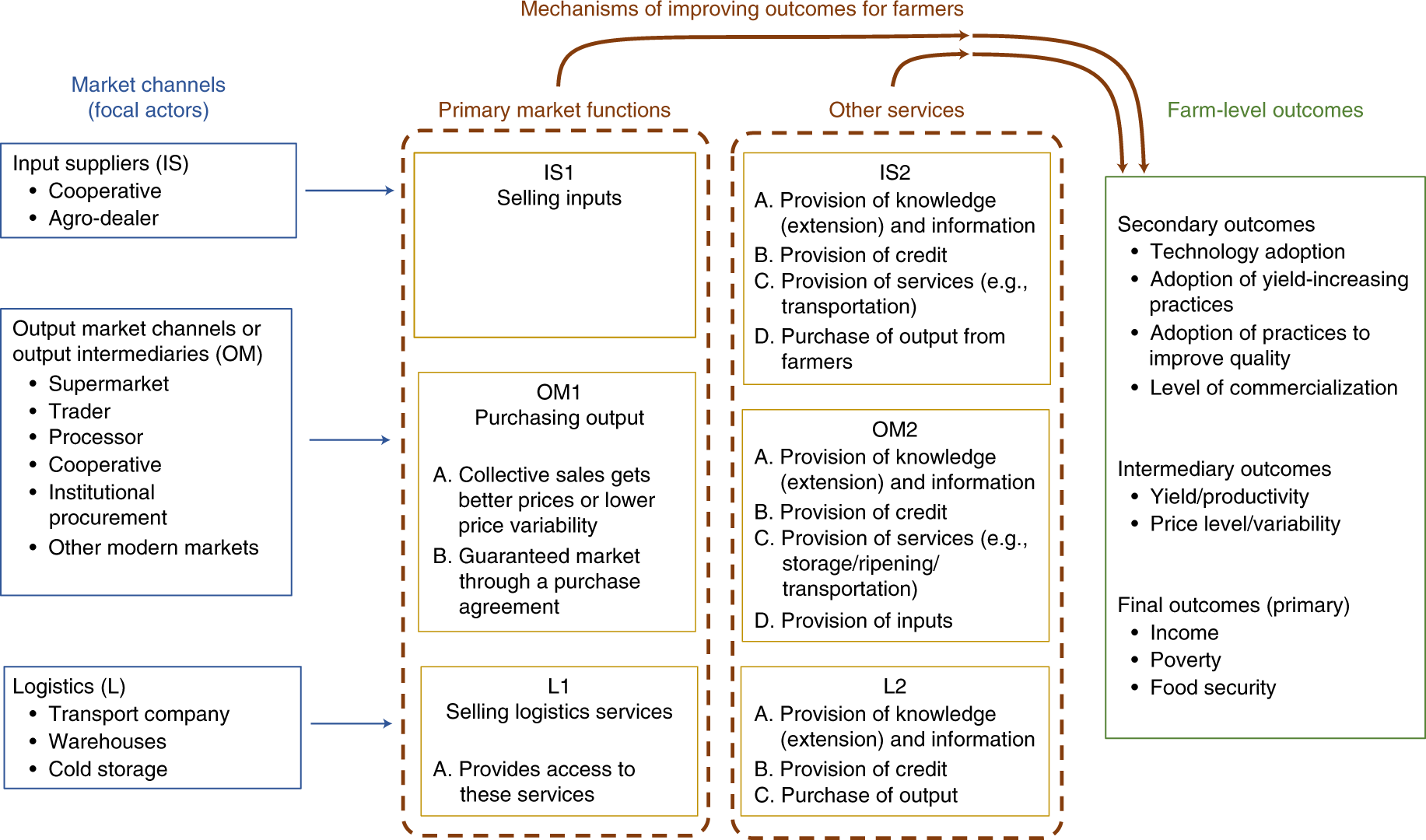
A scoping review of market links between value chain actors and small-scale producers in developing regions | Nature Sustainability
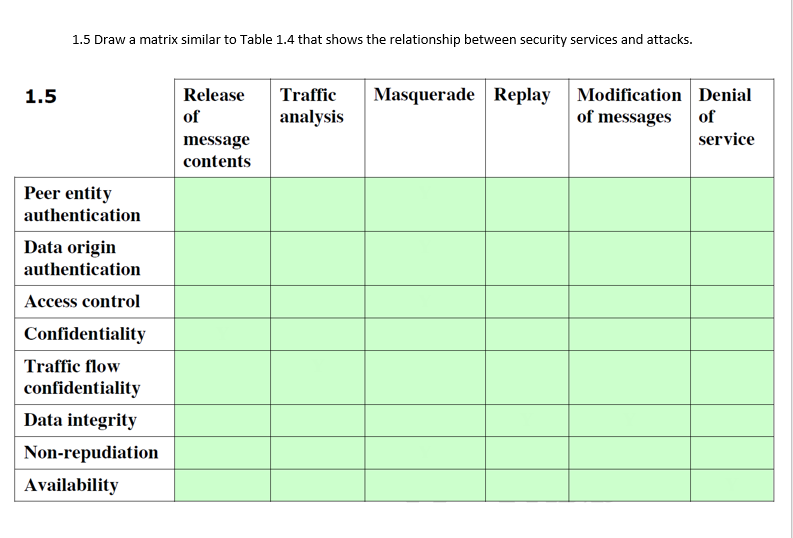
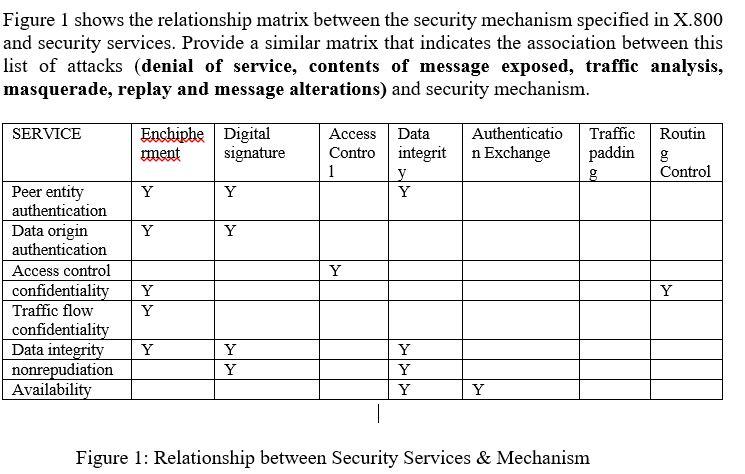
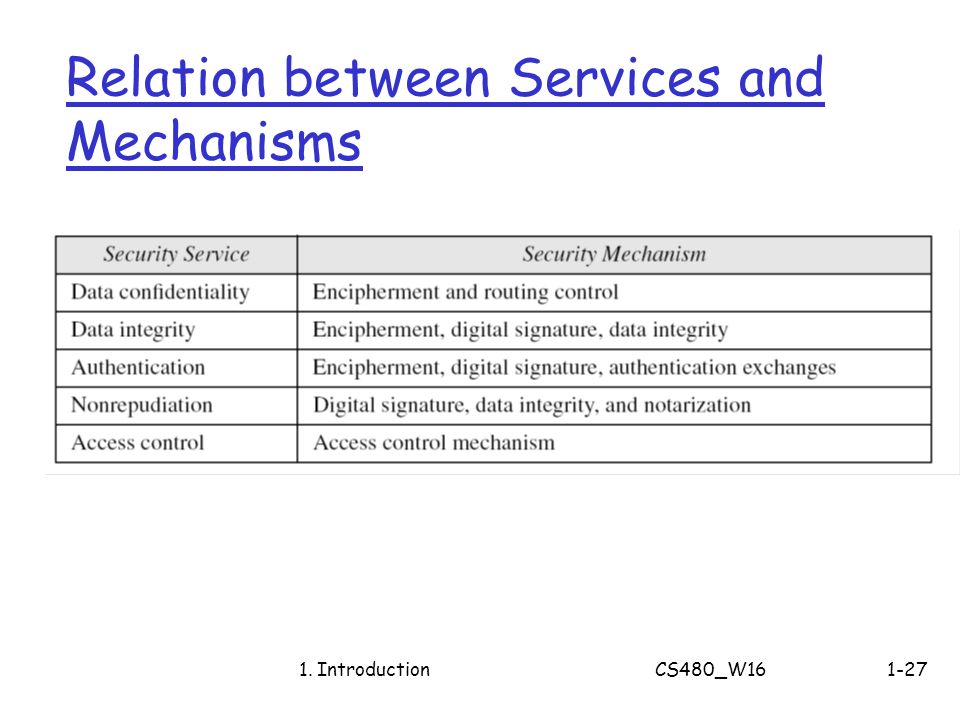
Network security essentials - chapter 1 - 7 Draw a matrix similar to Table 1.4 that shows the relationship between security services and | Course Hero
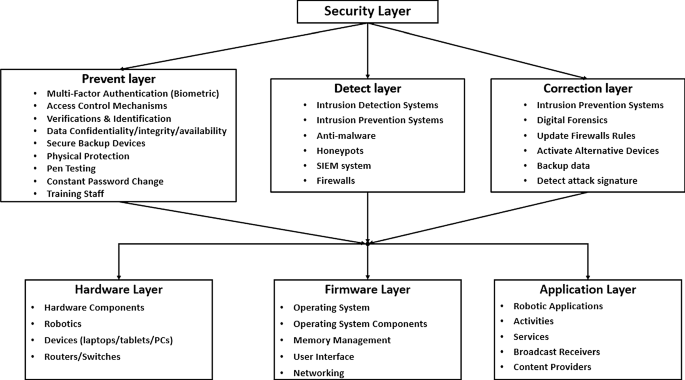
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink

Table 3 from Trusted third party services for deploying secure telemedical applications over the WWW | Semantic Scholar